6G7V0031: Advanced Network Security Assignment Brief | MMU
Learning Outcomes:
LO1: Critically analyse and evaluate the current and emerging trends in network security and its deployment in an organisation.
LO2: Identify and conduct the high-level design of secure network applications.
Assignment Tasks
1. Overview
In this assignment, you will identify one of the cybersecurity state-of-the-art topics of your choice. You will create a technical report, critically analysing the latest research articles under the chosen topic. Further, you will highlight the limitations/research gap in the literature and come up with your idea to overcome it.
Task 2 expands on Task 1, where you will create a presentation and submit a concise video.
In the third task, you will use industry-standard tools (Wireshark) to analyse and interpret packet captures containing attack traffic. You will report suspicious and malicious behaviour exists in the traffic.
Task 1 – Network Security Research Report
For this task, you will choose an advanced cybersecurity topic. Under the chosen topic, you will analyse the most recent literature, highlight a research problem/identify a research gap/limitations in the literature, and propose your approach/solution to address this problem or gap.
Your report should be precise and must include the following:
- Title: Indicates the topic and scope of the work.
- Introduction to the topic along with the rationale for selecting it.
- Literature review: Critically analyse literature (research papers, whitepapers, technical reports,online articles) and highlight research gaps or limitations.
- Proposal: Your idea to overcome the limitations.
o A new algorithm, systems, frameworks, protocols, tools, best practices, government regulations, etc. - References: IEEE Format
- Structure of the Report: Title, organization, and citations of references.
Are You Looking 6G7V0031 Assignment for an Answer of This Question
Order Non Plagiarized Assignment
Task 2: Showcase (Video submission)
You need to create presentation slides and produce a short video and submit it via moodle under 1CWK20 submission link. Utilize the content from Task 1 to produce this video, ensuring that it encompasses the following aspects.
1. A brief introduction of the topic.
2. Research Gap/limitations in the literature.
3. A schematic representation of the proposed solution to address the limitations.
4. The potential impact of your solution/proposal.
Task 3: Analysing Network Traffic (Wireshark)
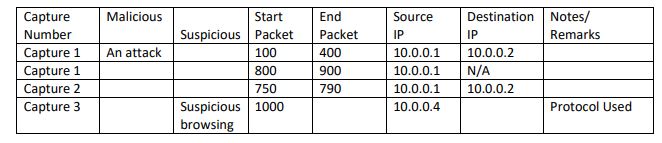
You have been provided with a collection of pcap files, each containing network traffic. You will analyse traffic of each capture to differentiate malicious and suspicious traffic and complete the table below; you may include multiple entries per capture as per the example:
3. Assignment Marking Scheme
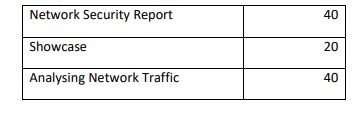
See the accompanying marking scheme below for a more detailed breakdown of the allocation of marks.
4. What to hand in
You will need to submit your individual report through Moodle submission inbox, which is highlighted at the top of the unit Moodle area. In 1CWK80, you will need to submit your report Task 1 and Task 3 as one PDF fil. Please use the following naming structure for your report before uploading it to Moodle (“your lastname-firstname-studentID.pdf”). In 1CWK20, you need to capture a video of your presentation and submit it through Moodle
